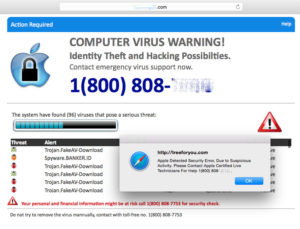
A fake computer virus warning on a Mac
I have had several clients contact me after having responded to a scary notice on their computer screen that said their computer had been hacked and recommending that they call the toll free 1-800 number listed to reach a so-called Microsoft tech support service. Some of these warning screens are accompanied by scary music or tech failure sounds. Many clients gave their credit card number to the fake tech support person at the other end of the call and allowed them to log onto their computer to remove the supposed “malware infection”. In fact, the pop-up notice was itself malware, which is why it wouldn’t go away. In most cases the fake tech support people then fix a lot of problems that don’t exist in exchange for several hundred dollars worth of “protection” for one year. It reminds me of the Mafia’s old protection racket. A gangster would visit every retail small business in the neighborhood and offer them protection services for a monthly fee, with the warning that if they didn’t pay up, “something terrible could happen”. It was a thinly veiled threat in the guise of a helpful warning. And of course, if the business owner didn’t agree to the protection, terrible things did happen.
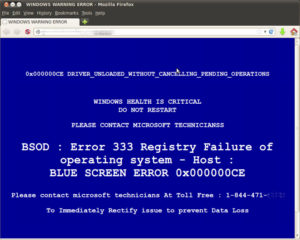
A fake computer crash warning on a PC
Please, don’t fall for it. If you get one of those scary pop-up notices, call a bona fide computer support specialist, not the 1-800 number on the computer screen at that moment. If you did fall for it, first call your credit card company and ask them to cancel the charge. They will probably understand very quickly, as this type of scam is well documented. Second, call us or another tech support company to help purge your computer of any software the fake tech support person installed on your PC or Mac. (Yes, this scam can affect Macs too). You’ll probably come out of the experience with all your precious data intact and all the bugs removed from your computer. You’ll also be wise to the scam, in case it ever happens again.
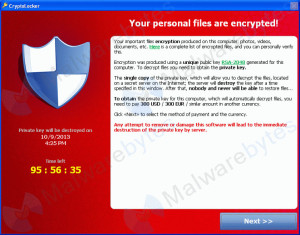
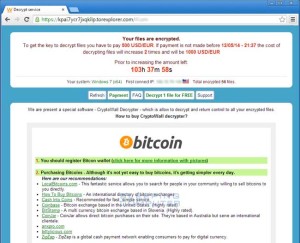
Note: This scam is different from a “ransomware attack”, which is discussed in a previous article on this site.

 Sometimes after removing a computer virus from a infected Windows PC it looks as though all the user’s documents and programs are GONE. This can cause a panic for the user, not to mention the unseasoned technician. Usually nothing is actually gone, the apparently missing items are just hidden. Here’s a simple fix if this happens to a Windows XP machine:
Sometimes after removing a computer virus from a infected Windows PC it looks as though all the user’s documents and programs are GONE. This can cause a panic for the user, not to mention the unseasoned technician. Usually nothing is actually gone, the apparently missing items are just hidden. Here’s a simple fix if this happens to a Windows XP machine: