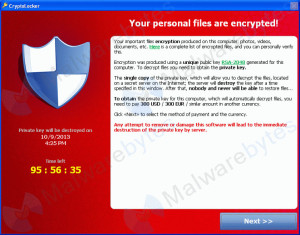
CryptoLocker Ransomware – If you see this on your computer screen you are in trouble.
Of all the computer viruses I’ve seen in nearly 20 years of helping people with their computers, none is nastier than what is known as “ransomware”. There have been several variations, starting with a virus called Cryptolocker. Later versions were called CryptoDefense and CryptoWall, just to name a couple. They use a powerful kind of encryption to render all of your personal files impossible to open without the encryption key. They ransom that key to the owner for as much as $1,000 US, but that could go up at any time. To increase the urgency of paying the ransom, they warn you that if you don’t pay within a day or two, the “fee”doubles in cost. If you miss the last deadline they say they destroy the encryption key.
Unlike other viruses, removing the virus does not restore access to your files. Unless you have the files backed up to an external source – either a drive not connected to your computer since getting the virus, or online backup (in “The Cloud”), your files are gone. Of course you could pay the ransom, but there is no guarantee that you will get the encryption key in exchange, since you are dealing with crooks. Many people have reported paying the money and not getting the encryption key, or it not working. Obviously, the crooks are not big on technical support.
Besides having a good, up to date antivirus program on your PC, the best defense against threats such as ransomware is to have a reliable, automatic and frequent backup program running, preferably one that keeps prior versions of changing files. We have discussed automatic online backup services in an earlier post. There is no substitute for good, frequent backups. In the case of ransomware, it’s not only the best defense, it’s often the only defense. If you back up to an external hard drive that is connected to the computer after you get the virus, your backed up files will also be inaccessible.
Once the virus is removed, if you are lucky you may be able to recover some or even all of your files, provided your operating system is Windows Vista, 7 or higher. Removing the virus is a fairly advanced technical feat, but one which is outlined in a video on YouTube.com. If you have Windows Vista or later you may be able to recover an earlier version of the file through a Windows background feature called Shadow Copy, although later variants of the virus may delete the Shadow Copy backups, as well as System Restore points. Again, the best defense against this type of virus is to have good and frequent backups. If your backup drive is connected to the computer at the time of your infection, all the files on the backup drive may be encrypted as well. That’s why online backup in addition to local backup is so important.
Besides having a good and up to date antivirus program on your PC, I recommend using “second opinion” antivirus software such as SurfRight’s Hitman Pro. This does not conflict with your main antivirus software, and it may catch infections that the primary program misses.
The image below is a screen shot of the CryptoWall ransomware instructions for paying the perpetrators through Bitcoin. Paying it is not a good idea.
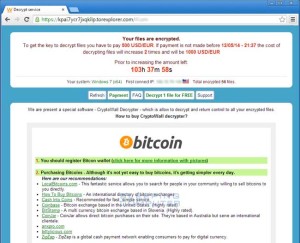
The CryptoWall ransomware page.
